Store SSH Keys Securely

Let me tell you how you can safely store SSH keys on a local machine, for not having a fear that some application can steal or decrypt them.
This article will be especially useful to those who have not found an elegant solution after the paranoia in 2018 and continue storing keys in $HOME/.ssh.
To solve this problem, I suggest you using KeePassXC, which is one of the best password managers, it is using strong encryption algorithms, and also it have an integrated SSH agent.
This allows you to safely store all the keys directly in the password database and automatically add them to the system when it is opened. Once the base is closed, the use of SSH keys will also be impossible.
First we need to add SSH-agent to autorun at login. For achieve this, open ~/.bashrc in your favorite editor and add to the end:
SSH_ENV="$HOME/.ssh/environment"
function start_agent {
echo "Initialising new SSH agent..."
/usr/bin/ssh-agent | sed 's/^echo/#echo/' > "${SSH_ENV}"
echo succeeded
chmod 600 "${SSH_ENV}"
. "${SSH_ENV}" > /dev/null
}
# Source SSH settings, if applicable
if [ -f "${SSH_ENV}" ]; then
. "${SSH_ENV}" > /dev/null
#ps ${SSH_AGENT_PID} doesn't work under cywgin
ps -ef | grep ${SSH_AGENT_PID} | grep ssh-agent$ > /dev/null || {
start_agent;
}
else
start_agent;
fiAfter that we need to enable support in KeePassXC:
Tools → Setting → SSH-agent → Enable SSH-agent
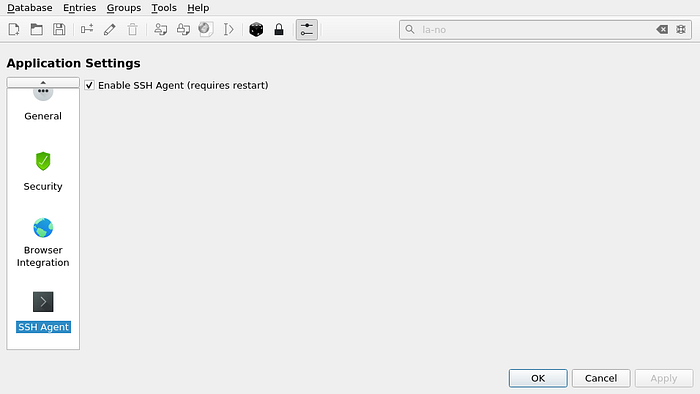
Setup is finished, now let’s try to add a new SSH key into KeePassXC:
Click on the key button, then fill in the data:
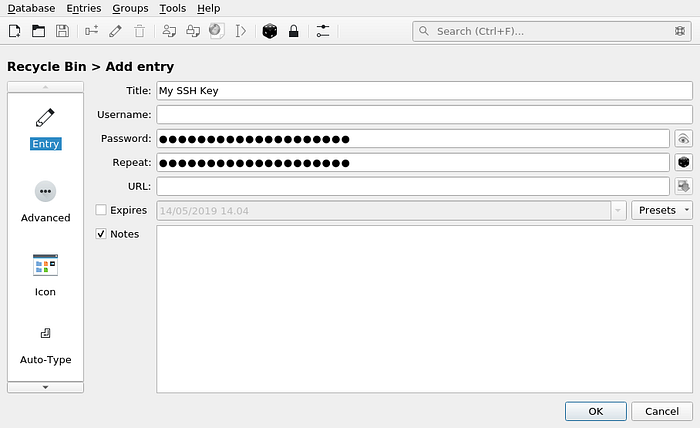
If the key is password protected, don’t forget to specify the password phrase.
On the Advanced tab, load your id_rsa as an attachment:
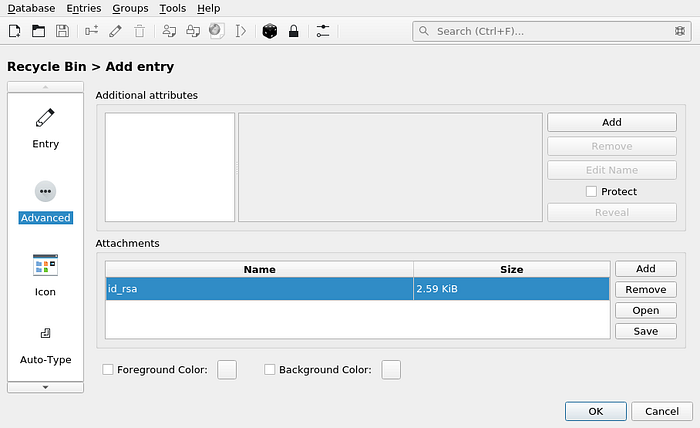
On the SSH Agent tab, tick checkboxes:
- Add key to agent when database is openned/unlocked
- Remove key from agent when database is closed/locked
Next, choose our key (id_rsa) in the Attachments.
And click the Add to Agent button:
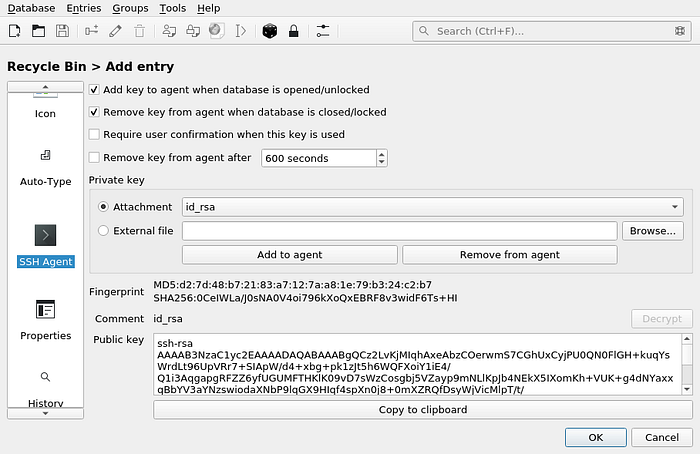
Now when KeePassXC is running, the key will be automatically added to the SSH agent, so you can no longer store it on disk!
